Firefox Security Newsletter/FSN-2019
Contents
Firefox Security Newsletter - 2019 in Recap
Maintaining and building a secure modern browser is one of the most challenging tasks in software engineering. You’re up against sharp competition from other browsers and an incredibly large ecosystem of malicious actors and white-hat security researchers. To keep up you need a great team. Working on Firefox, I pride myself with being surrounded by some of the best browser engineers in the world. In this blog post, I wanted to share what we all have been up to in 2019.
In the future we’ll be publishing this update quarterly, using a few categories, with explanations for what they mean right below their headlines.
It is of course impossible to present the vast amount of work that went into each of the highlighted projects in a single blog post, so I highly recommend following the links to read more about the individual efforts.
Privacy
This is our work to deliver a more private experience on the web to all Firefox users.
A big focus of 2019 was the Anti-Tracking project. With the 69 release we shipped ETP (Enhanced Tracking Protection) to all Firefox users by default. This was a huge milestone for the team and for privacy on the web overall.
In addition to our anti-tracking efforts, we also shipped protections from cryptomining, fingerprinting and social networks that were tracking users through the web.
To highlight these new features, the team built an entirely new Protections UI, that consists of a new panel in the address bar as well as the new about:protections page that allows users to get an overview of their active protections.
In addition to our default-on tracking protections, the privacy engineering team also works with the Tor Browser team to develop and integrate more advanced origin isolation and anti-fingerprinting techniques intended for usage in the Tor Browser. Sometimes those techniques start in Tor Browser and move to Firefox; other times they start in Firefox and move to Tor Browser. The most prominent example of this work in 2019 was Letterboxing, a way for the browser to shrink the content viewport to make it less unique.
In an effort to improve our coverage of Origin Attributes across the code base, Paul Zühlcke added support for handling OAs in the Firefox permission manager. This means that web permissions can now be scoped by private browsing window, per container or using first party isolation.
Steven Englehardt wrote a summary of our progress on privacy-preserving telemetry with Prio. We landed the necessary pieces to perform the privacy-preserving origin telemetry in Nightly and will be testing it before deploying further to Release.
The Facebook Container team shipped Facebook Container 2.0, with significant improvements to our extension that keeps Facebook from tracking you around the web for good.
Core Security
Core security, for us, means efforts to protect Firefox from vulnerabilities and exploits. This work is usually not exposed to users, but everyone benefits from having a rock-solid secure browser.
In 2019 we shipped 4 security-related “chemspill” releases, meaning urgent dot-versions of Firefox (e.g. 72.0.1) that contained especially urgent security fixes. Each of these chemspills went out within a day!
Several teams concentrated their efforts on Hardening the Firefox Security Architecture, with a particular focus on sandbox escapes. Listed below are the main projects that were part of this effort.
We improved our protection against JavaScript code injection in browser UI or other privileged areas of code (e.g. about: pages). To this end Gijs prevented untrusted pages from being loaded in the parent process. Christoph Kerschbaumer applied CSPs to all of our about: pages. Jonas Allman and Tom Ritter removed and disallowed usage of eval() in the parent process and system privileged code. Freddy Braun disallowed non-internal resources do be loaded as documents in privileged contexts. More efforts of this type are underway in 2020.
Zombie reduced the possibility of sandbox escapes through malicious IPC messages by ensuring that IPC messages claiming to come from the extension process do, in fact, come from an actual web extension.
The Hardening team, in conjunction with the Low Level Tools team, deployed memory partitioning, isolating particularly powerful attacker-controlled objects like Strings and ArrayBuffers from other DOM objects, as well as additional guard pages around certain types of memory structures.
Jed Davis gave us the ability to share memory with a content process, but freezing it so the content process cannot write to it.
A big effort in 2019 and also in 2020 is the Fission project, that aims to achieve true process isolation per site. This is a very extensive project that involves rewriting large parts of the browser and engine code. In 2019 we achieved a number of milestones for Fission progress, such as implementing DocumentChannel (a refactoring of how navigation occurs), building a multiprocess browser toolbox, burning down a lot of test failures. Fission will continue in 2020 where we expect to have something everyone can turn on and report any issues with.
The Browser Architecture team was able to remove the last traces of XBL from Firefox code, eliminating a lot of old code and some obvious attack surfaces for sandbox escapes along the way.
Jonas integrated Project Wycheproof for testing our NSS cryptography library.
The Fuzzing team added new targets this year, such as Necko (the Gecko networking stack) and IndexedDB and published the Grizzly Browser Fuzzing Framework.
The Platform Security team deployed our most restrictive sandbox yet in the Media Decoder process on Windows and OSX, and made considerable progress on our multi-year effort to remove win32k from the content process on Windows.
With considerable help from :dmajor, the Platform Security team deployed a limited form of Control Flow Guard support for Windows, with hopes of expanding it in 2020.
Haik spent a considerable amount of time to support Catalina’s new required software notarization scheme and hardened runtime support.
Aaron Klotz and Toshihito Kikuchi worked to improve our telemetry and insight into third party modules that inject in our process on Windows.
With the help of a UCSD research team, we compiled the graphite font rendering library as wasm, enclosing it in a sandbox with data validation. Currently supported on x64 versions Linux and OSX, this allows us to turn a C library into a memory safe language and firewalling it from the rest of the process. Future expansion to new libraries and Windows are underway.
Firefox Security
Firefox Security means user-exposed security features that allow you to have a safe experience on the web.
The Firefox Lockwise team significantly revamped the desktop password manager experience, bringing Lockwise to desktop. New features include a new password management UI (about:logins), secure password generation, integration with Firefox Monitor and more improvements and bugfixes.
We released the Beta version of an entirely new product in the Firefox family: Firefox Private Network, a VPN and Proxy solution by Mozilla.
Our interns Carolina and Danielle built an entirely new Certificate Viewer (about:certificate) for Firefox, modeled after the popular Certainly Something browser extension which itself was developed by April King, another Mozilla engineer.
The DNS-over-HTTPS project aims to improve the problematic privacy and security properties of DNS for our users. In 2019, the DoH team ran experiments and added a way for parental controls providers to disable DoH, in preparation for the upcoming launch.
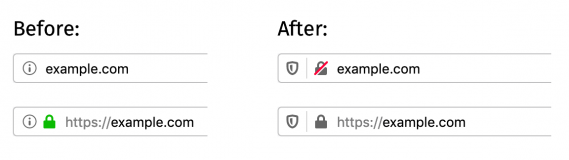
The Firefox 70 release brought us new improved security UI indicators, with a new indicator for insecure HTTP connections, as well as a reduced level of presentation for Extended Validation certificates.
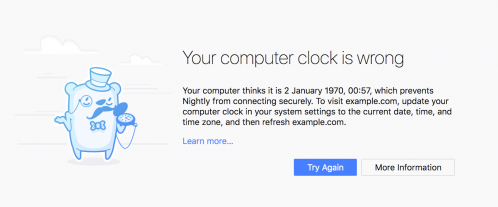
We shipped an updated design for our certificate error pages (built by our Outreachy intern Trisha Gupta) including a brand new error page highlighting when the local system time being off is likely at fault for the error.
In an effort to reduce breakage from Anti-Virus and other software that tries to intercept connections without installing their root certificate in the Firefox cert store, the team built a mode where Firefox can automatically detect MitM-related certificate errors that would be fixed by importing certificates from the OS root store. In addition to that, there’s now a message shown in the identity popup when the site is verified by an imported root certificate.
The Firefox Add-on Manager now includes an integrated abuse report mechanism, to help users quickly report malicious add-ons.
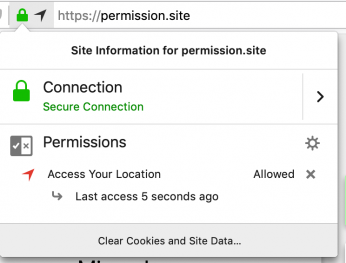
We improved our indicators for geolocation usage to include an in-use indicator and show when geolocation was last accessed by the site.
Web Security
This encompasses efforts to build features that allow web developers to build more secure sites. It sometimes also means restrictions made on web developers to *force* them to build more secure sites.
The Crypto Engineering team released Web Authentication in Firefox for Android.
We announced our plan to remove support for TLS 1.0 and 1.1 in March 2020. In 2019, we started rolling this change out to Nightly users and implemented a temporary override to allow early testers to avoid breakage.
After a series of experiments, we launched strong restrictions on notification permission prompts that will reduce the massive annoyance they presented to users of the web.
Johann Hofmann put web push notifications behind secure context. Ehsan Akhgari removed the ability for third party iframes to use web notifications.
In a cooperation with Cloudflare, the Crypto Engineering team started to experiment with Delegated Credentials for TLS, a mechanism which can alleviate trust concerns around distributing private keys to CDNs, without any of the performance overhead from alternative solutions.
Jonathan Kingston sent out an intent to remove AppCache, starting with Nightly and Beta in version 71 and to be unshipped in Release in 2020.
In several cases, Paul Zühlcke limited the ability for websites to spam window-modal dialogs, which were abused for DOS-style attacks to extort or confuse users.
Security Ecosystem
Our Bug Bounty program is getting a lot of love in 2020, and we kicked it off with two improvements in 2019: we significantly increased payments in the Mozilla Web Security Bounty Program and we created a static analysis bounty, adding CodeQL and clang to our Bug Bounty Program.
As part of encouraging more participation in the Bug Bounty program, we’re also working to provide walkthroughs that help people get involved. We published two blog articles specifically about the built-in HTML Sanitizer, where and how we rely on it, and how to get set up for testing it for bypasses in an iterative fashion in less than 30 seconds.
The MOSS Program funds development of open source software through grants; and also provides funding for security audits. Typically these happen in the background but every once in a while we discover something particularly impactful, like this Critical Security Issue identified in iTerm2.
The Mozilla Security Engineering University Relationship Framework (SURF) initiative hosted two conferences in 2019, in San Franscisco in May and in Vienna in November.
Steven Englehardt and Marshall Erwin published the first release of our anti-tracking policy.
Wayne Thayer announced version 2.7 of the Mozilla Root Store Policy.
As a reaction to the MitM attacks by the Kazakhstan Government using a custom root certificate, Firefox, in joint action with Google Chrome, blocked the use of the Kazakhstan root certificate.